Growth of Generative AI Is Augmenting Threat Landscape
End-user spending on security and risk management (SRM) in the Middle East and North Africa (MENA) region is forecast to total $3.3 billion in 2024, an increase of 12.1% from 2023, according to a new forecast from Gartner, Inc.
“The rapid growth of generative AI (GenAI) is expanding the threat landscape. At the same time, the evolving regulatory landscape and the alarming frequency of cyberattacks are prompting SRM leaders to increase their spending on security measures,” said Shailendra Upadhyay, Senior Research Principal at Gartner.
“Organizations are also strategically improving their defenses by adopting advanced technologies and security solutions which enable them to proactively identify potential vulnerabilities or malicious activities across various digital platforms.”
Gartner analysts are discussing ways to enhance the flexibility and responsiveness of SRM techniques and technology at the Gartner Security & Risk Management Summit, taking place in Dubai .
In 2024, spending on data privacy in MENA is projected to record the highest growth rate of all segments, increasing 24% year-over-year (see Table 1)
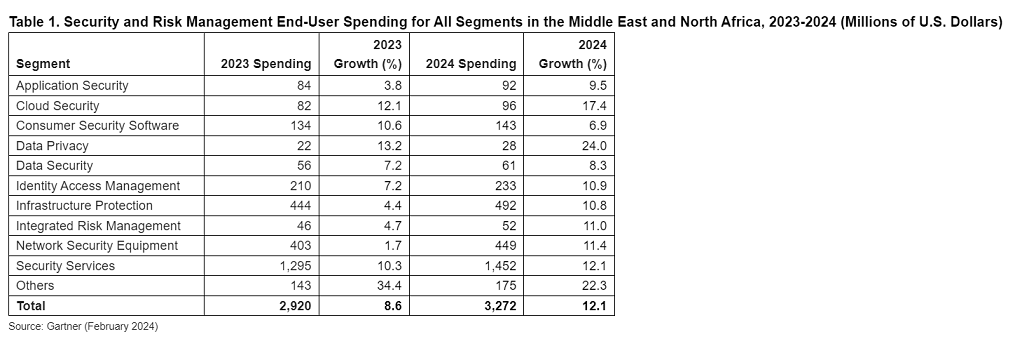
“In accordance with the European Union’s General Data Protection Regulation (GDPR), the Gulf Cooperation Council (GCC) has recently implemented data protection laws for handling personal data of identifiable individuals,” said Upadhyay. “These laws require MENA organizations to maintain a higher standard of data privacy and cyber security measures, resulting in an increase in spending on data privacy.”
Cloud security spending is expected to record an increase of 17.4%, the second highest growth rate in 2024. The growing use of infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS), is projected to drive spending on cloud security resources. The adoption of multi-cloud environments has also resulted in increased security complexities, which has boosted the demand for cloud-based detection and response solutions, such as endpoint detection and response and management tools.
Most Critical Cybersecurity Trends in 2024 for MENA CISOs
The appearance of GenAI as a mainstream capability is causing significant disruptions in digital and business sectors. Gartner predicts that GenAI will cause a spike in the cybersecurity resources required to secure it, causing more than a 15% incremental spend on application and data security by 2025.
To effectively manage GenAI challenges and tackle other external factors, such as a shortage of security talent, growing regulatory concerns, and the rapid adoption of cloud technology, CISOs must prioritize two top cybersecurity trends. They will help improve organizational resilience and the performance of the cybersecurity function.
Exploring the Potential and Perils of GenAI – Large language model (LLM) applications, such as ChatGPT and Google Bard, have put GenAI on the agenda for inclusion in many business, IT and cybersecurity roadmaps.
“GenAI creates new attack surfaces, which security leaders must be ready to defend,” said Jon Amato, Senior Director Analyst at Gartner. “To reduce the risks of GenAI, application and data security programs must adapt to accommodate this new way of using the technology to do business.”
Organizations must establish policies that govern the use of GenAI applications and develop training and guidance modules. This will help minimize unauthorized use of GenAI and decrease the risks of privacy and copyright infringement. Additionally, companies should update their application and data security practices to incorporate new attacks, such as the prompts or orchestration layers used to control AI models.
Security Behavior and Culture Programs – The democratization of GenAI amplifies security challenges that organizations can face. Democratizing GenAI enables employees to have unrestricted access to powerful technical capabilities that, if used without due care, could result in data breaches.
Organizations need to implement security behavior and culture programs (SBCPs) to minimize cybersecurity incidents associated with employee behavior, whether inadvertent or deliberate. “Implementing effective SBCPs requires greater support and time commitments from senior executives and a shared vision of a secure enterprise that everyone in the organization can understand and support,” said Amato.

