Positive Technologies: cyberattackers targeting telecommunications and the military-industrial complex in the Middle East
The region’s most-attacked countries are Saudi Arabia and the UAE
Positive Technologies has conducted a comprehensive research into the activities of the APT groups targeting organizations in the Middle East . The experts say that 88% of the groups under review were attacking Saudi Arabia, and the five most-attacked sectors were government agencies, manufacturing, telecommunications, the military-industrial complex, and energy. To gain initial access, malicious actors mostly sent phishing email and exploited vulnerabilities in public-facing applications.
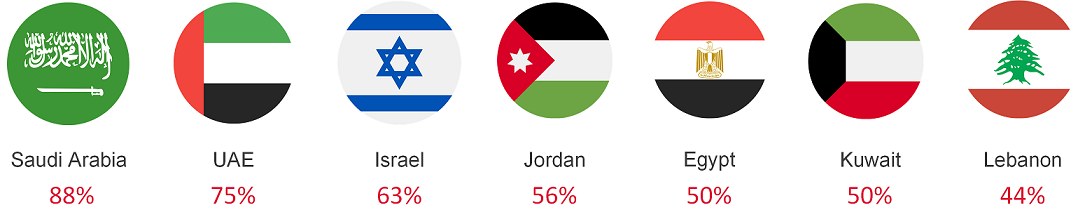
According to the analyzed data, malicious actors’ seven key targets were Saudi Arabia (88%), the UAE (75%), Israel (63%), Jordan (56%), Egypt (50%), Kuwait (50%) and Lebanon (44%) .
“An overwhelming majority of APT groups active in the Middle East had attacked governments (94%) and industry (81%) at least once, and 69% had attacked the energy sector,” says Yana Avezova, a senior analyst with the Positive Technologies research team. “It is worth noting that government agencies were the most attractive targets for all malicious actors: in 2022–2023, these accounted for 22% of total attacks on organizations in the Middle East.”
According to the report, two of the five most-attacked sectors, targeted by half of all groups, were telecommunications and the military-industrial complex (MIC).
The Positive Technologies believe that the MIC rose to the top of the rankings due to the specific nature of the region. Compared with other regions of the world, Middle Eastern media, too, have often found themselves a target of cyberattacks and historically have ranked high on the list. Experts attribute cybercriminals’ heightened interest in the telecommunication sector to attacks by China-linked groups, as telecoms have long been one of their targets of choice.
According to the analysis by Positive Technologies, the methods of obtaining initial access varied: 69% of groups relied on phishing email campaigns, 31% exploited flaws in public-facing applications, and 19% deployed malware on industry websites.
“Complex, targeted attacks begin with reconnaissance,” says Alexander Badaev, an information security threat researcher at Positive Technologies Expert Security Center. “Attackers may conduct extensive network scanning to identify suitable targets. This gives them enough information for the initial stage of penetration. The information may include a list of applications installed on the target server and its versions containing known vulnerabilities. After reconnaissance comes the preparation of tools for the attacks. Cybercriminals may register fake domains and create email or social media accounts for spear phishing.”
According to Badayev, after successfully gaining initial access, the attackers seek to establish a foothold in the infrastructure. To do this, 69% of APT groups leveraged the task scheduler, an OS component that runs applications or scripts at a predefined time or in response to a certain event, as in the case of a campaign that targeted the UAE government, where a group named OilRig created a MicrosoftEdgeUpdateService scheduled task that ran every five minutes, launching malware. Most attackers (56%) configured malware to auto-run. A third of APT groups (31%) gained a foothold in victim companies’ systems by setting up malware to run on a certain event.
After penetrating a corporate network, attackers examine the devices they have managed to gain access to, to understand how to proceed. According to the analysis, 94% of groups looked for data on the operating system and architecture of the compromised host, and information about software versions, installed patches, and updates. A large number of groups (81%) sought to identify the users of the compromised host and find how active they are, 63% looked into processes running on the compromised hosts, and 56% searched files and directories for useful information.
It is crucial for APT groups to remain undetected in the compromised environment for as long as possible, says Positive Technologies. Adversaries employ various methods to hide traces of their presence. They typically pre-test samples of their malware and subsequently modify these to bypass antivirus detection. A common technique is to disguise malware as legitimate files or applications. Over half (56%) of APT groups removed signs of their activity by clearing event logs and network connection history, and modifying timestamps. This makes it much more difficult for cybersecurity professionals to investigate the incident.
To build effective defenses against complex targeted attacks, Positive Technologies recommends that organizations pay attention to the fundamentals of results-oriented cybersecurity, which includes the following:
• Asset management
• Incident monitoring and response
• Cybersecurity training
• Security assessments
The full list of tactics and techniques used by APT groups active in the Middle East is available in the report published on the website.